Safeguard Your Business with Cast DDoS
Proactive, real-world simulations to identify vulnerabilities, enhance resilience, and meet compliance needs.
Overview
In today’s digital landscape, securing your business data is more important than ever. Many organizations test their infrastructure annually due to regulatory obligations, leaving potential vulnerabilities unchecked. Cast DDoS transforms reactive testing into proactive management with continuous testing and real-time visibility, ensuring your infrastructure remains secure, resilient, and optimized.
As compliance regulations like the SEC’s cyber resilience rules and the EU’s Digital Operational Resilience Act (DORA) evolve, Cast DDoS helps you stay ahead, protecting your assets, minimizing risks, and enhancing performance.
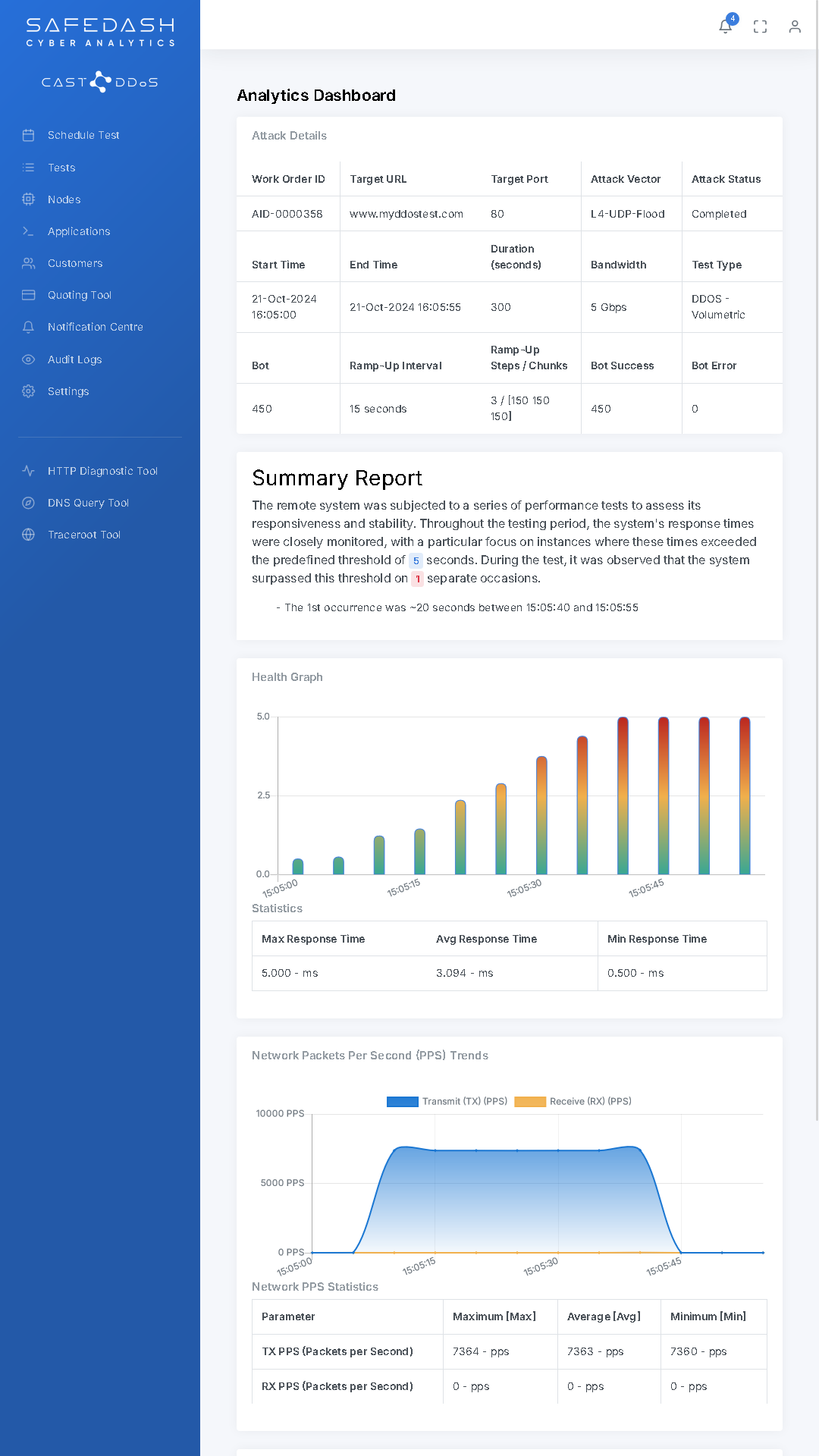
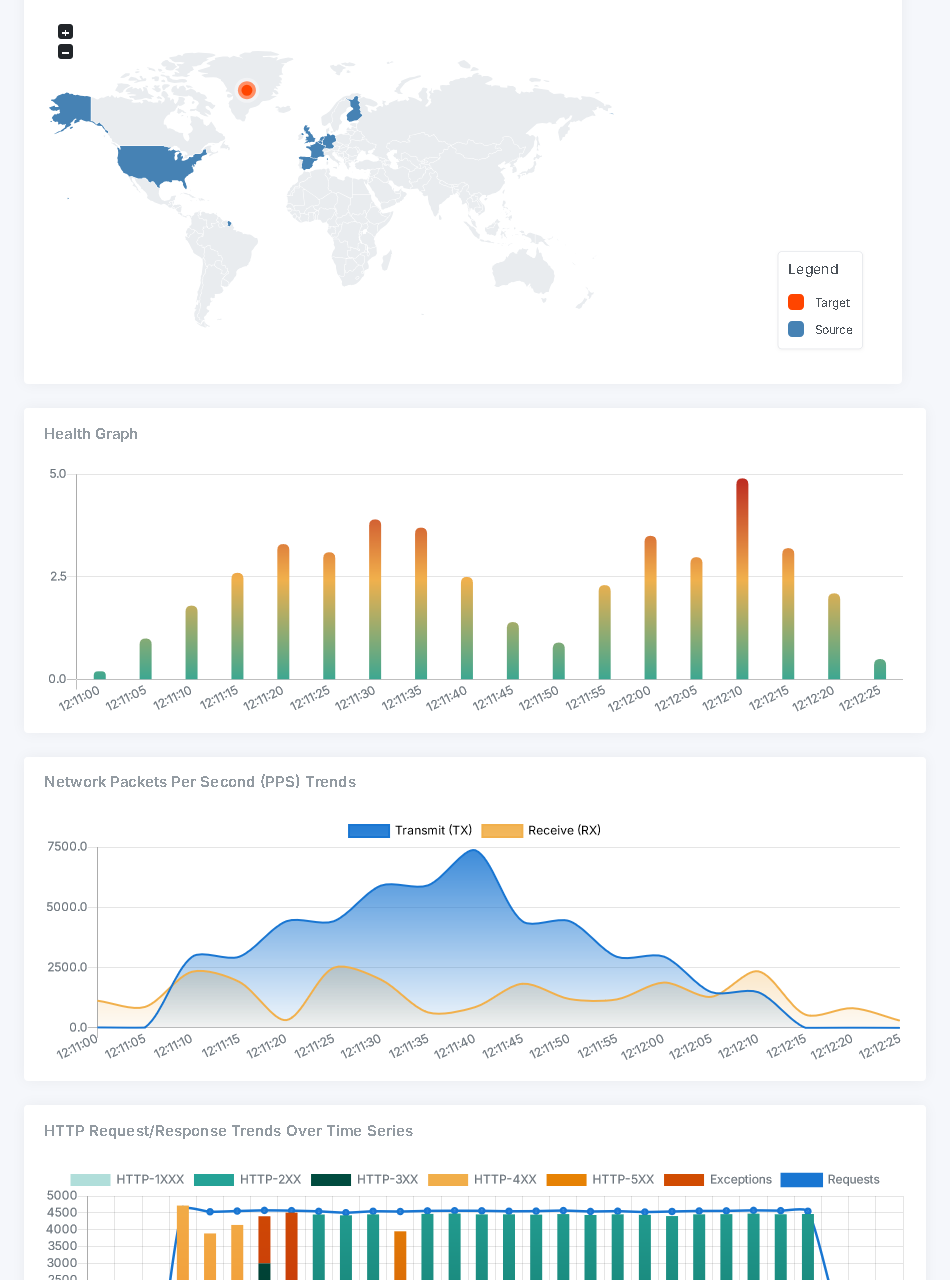
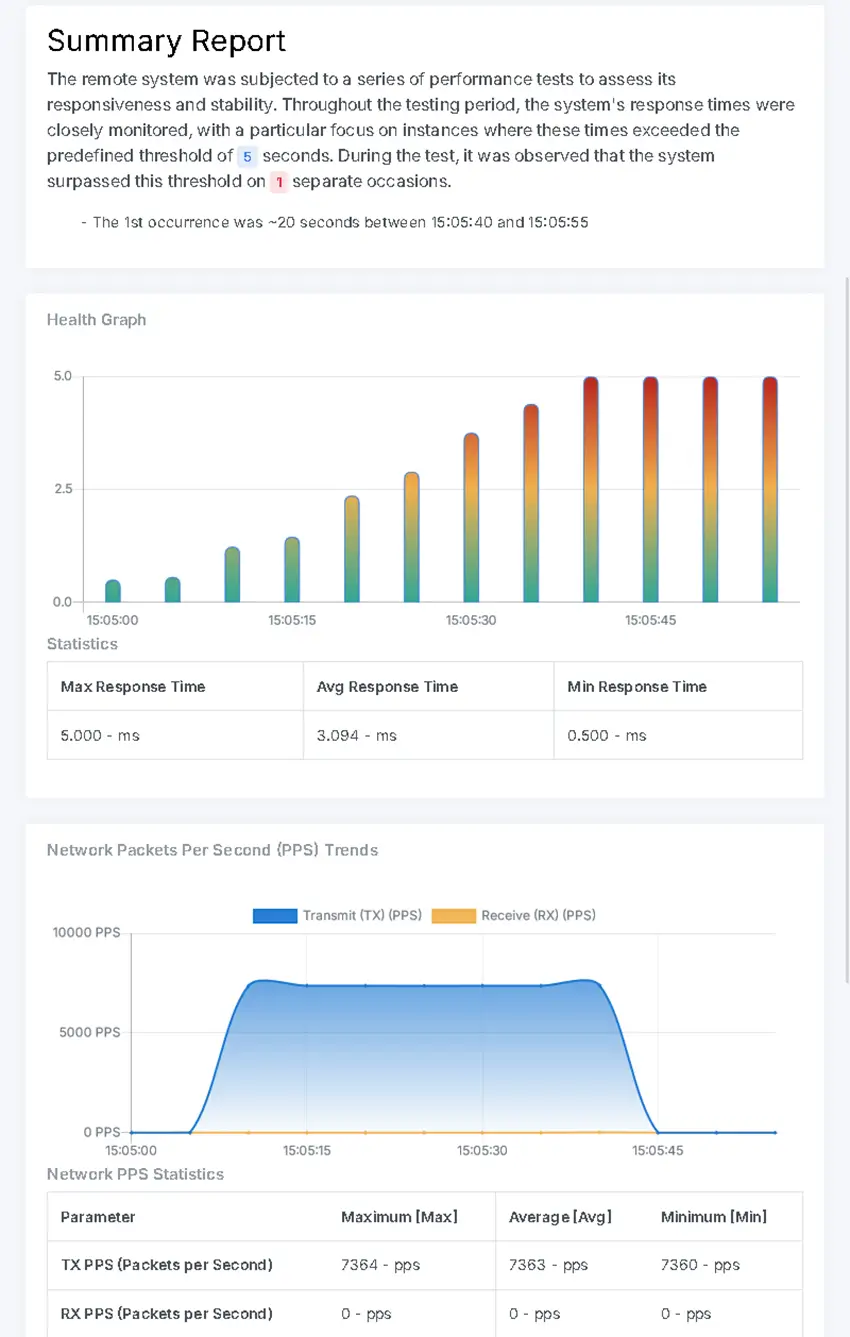
DDoS attacks are frequent and highly damaging. Yet, simulating these complex attacks remains a challenge for many businesses. Cast DDoS offers near-realistic simulations, designed by white-hat experts, to help you identify vulnerabilities and test your mitigation strategies. Our cloud-based platform generates controlled attack traffic that mirrors real-world threats, allowing you to:
- Assess network resilience
- Identify weaknesses
- Refine your defenses
Request a Callback
Cast DDoS Key Features
Near-realistic simulations
Replicate real-world DDoS attacks to accurately assess your network's resilience.
Continuous testing
Identify vulnerabilities proactively and stay ahead of evolving threats.
Real-time visibility
Gain insights into your network's performance and identify potential weaknesses.
Compliance-driven
Ensure adherence to industry regulations and protect your organization from legal risks.
Customizable Simulations
Tailor tests to your specific needs and threat profile.
Scalable Simulations
Adjust testing to fit your network's size and complexity for comprehensive coverage.
The Safedash Advantage
We're more than just a provider of cybersecurity tools; we're your partner in building a resilient digital future. Contact us today to learn how Safedash can help secure your business.
How Cast DDoS Can Help You
Prevent Downtime
Proactively identify and address DDoS vulnerabilities to prevent costly downtime and operational disruptions.
Reduce Financial Losses
Protect your revenue streams and reputation by minimizing the impact of DDoS attacks.
Optimize Resource Allocation
Identify where to deploy security resources for maximum protection against DDoS threats.
Vendor Benchmarking
Ensure you're getting the best value from your security vendors by comparing performance.
Staff Training
Train your team with hands-on simulations and drills to effectively prevent and respond to attacks.
Protect Your Uptime, Revenue, and Reputation with Cast DDoS Solutions.
Case Studies
Case Study 1: Enhancing Anti-DDoS Configurations for an Insurance Company
An insurance company identified critical configuration issues in their Anti-DDoS setup. Cast DDoS simulations helped resolve vulnerabilities in their secondary connection, saving over $4 million by preventing 6 hours of downtime.
Case Study 2: Resolving Elastic Computing Issues for an Online Retailer
Through our DDoS simulations, an online retailer was able to resolve elastic computing issues, preventing 1 hour of downtime, saving them $12,820.
Case Study 3: Identifying Firmware Vulnerabilities in an Anti-DDoS Installation
Our DDoS tests uncovered firmware issues in a new installation for a distributor, helping them quickly identify vulnerabilities and prevent potential attack failures.
Case Study 4: Benchmarking Anti-DDoS Vendors for Optimal On-Prem Solutions
Cast DDoS helped a client benchmark two Anti-DDoS vendors, ensuring the client made an informed investment decision based on performance and protection against their specific needs.
Frequently Asked Questions
How do DDoS simulations benefit my organization?
Our simulations help you identify network vulnerabilities, test mitigation strategies, and prevent costly downtime and breaches.
What types of DDoS attacks do you simulate?
We simulate:
- Volumetric Attacks: High-traffic campaigns
- Protocol (Network-Layer) Attacks: SYN/UDP floods
- Application-Layer Attacks: Sophisticated Layer 7 threats
Will you need access to our network for simulations?
Yes, we’ll need access to your network to conduct realistic tests, ensuring full protection and isolation of your environment.
Can you stop the test in case of any issues?
Yes, we have an emergency stop feature to halt tests immediately if unexpected issues arise.
How often should we conduct DDoS simulations?
We recommend regular simulations based on your risk tolerance and regulatory requirements to stay ahead of evolving threats.
Can you simulate custom attacks?
Absolutely. We tailor simulations to match your organization's specific vulnerabilities and threat landscape.
